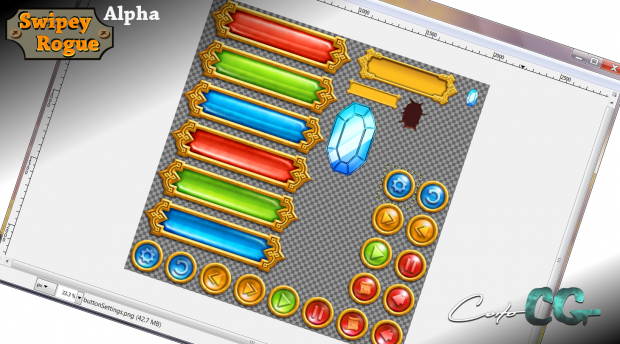
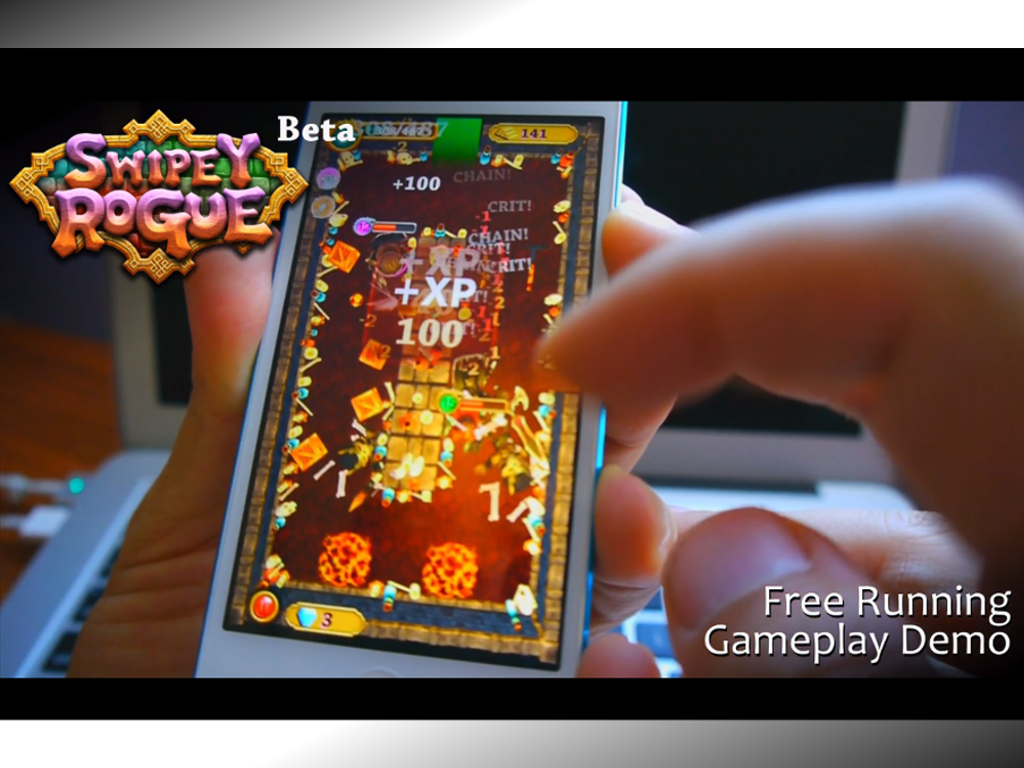
Mac OS X 10.13 or higher Safari 11, 12 or 13 JavaScript must be enabled Mac Secure Browser iPad Air 2 or newer. iOS 12 and up DATAMANAGER student testing app (App store download) Chromebook Chrome OS (current version) DataManager student testing app (Chrome Web Store download) 1366 x 768. Mac OS 10.8 'Mountain Lion', however, has dropped tcpwrappers from the operating system. If you do run hunt on a server connected directly to the Internet, use firewall rules to control who can connect to the huntd server rather than hosts.allow and hosts.deny. Swipey was a prominent recording artist for an independent label ‘Men of Principles.' Apart from collaborating with artists like Lil Durk and Shy Glizzy, Swipey was also associated with a group of rappers named ‘Squad Boyz.' He was also popular on social media as he had thousands of followers online. While his Instagram account has over. I wanted to play a rogue-like dungeon crawler on my phone, but I wanted something fast and engaging like an arcade runner or flyer. From these desires Swipey Rogue was born! While the target platform is definitely mobile devices, I intend to make PC/Mac/Linux builds as well.
Soundflower is an open source kernel extension for MacOS, designed to create a virtual audio output device that can also act as an input.
Initial development and maintenance of Soundflower was done by Cycling '74. In 2014, Cycling '74 passed stewardship of Soundflower to Rogue Amoeba, but we ultimately didn't have the time or resources to improve the product.
Thankfully, at the end of 2015, Soundflower's original author Matt Ingalls picked up the baton. The project can now be found via this GitHub link. If you're looking to use Soundflower, that's the link to visit.
If you've previously used Soundflower, or are simply looking for a reliable tool to route audio between applications on your Mac, you may be interested in Loopback.
Loopback
Loopback is a modern, fully-featured virtual audio device tool of our own. With a robust infrastructure and full support, it's the ideal tool to route audio between applications and more.
Learn more on the Loopback page.
Symptoms: Some clients are unable to connect to the internet. Some clients report a different IP address, subnet mask and default gateway, compared to others.
Caveats: Without a managed switch fabric, this is considerably more difficult.
Diagnosis:
1. Allow a device to get an IP address from the rogue server. You might need to disable the main DHCP server to allow this to happen, as DHCP is a broadcast protocol, so it's really a case of the early bird getting the worm.
1b: Kyle Gordon pointed out that this initially assumes that the DHCP server is the same as the default gateway. He suggests: Usually /var/lib/dhcpcd/*.info or /var/lib/NetworkManager/* will contain the dhcp-server-identifier info on Linux, and something in the Windows Event Logs will show similar :-) Narcolepsy mac os.
2. Once you've got an IP from the rogue, look at the ethernet adaptor's status, and get the IP of the default gateway. For this example, we'll call it 10.1.1.1
3. Ping the default gateway for a few seconds. We need to do this to populate the ARP table.
4. In a Powershell/Cmd/Terminal window, run the command to view the ARP table. On windows, this is `arp -a`.
Soundflower is an open source kernel extension for MacOS, designed to create a virtual audio output device that can also act as an input.
Initial development and maintenance of Soundflower was done by Cycling '74. In 2014, Cycling '74 passed stewardship of Soundflower to Rogue Amoeba, but we ultimately didn't have the time or resources to improve the product.
Thankfully, at the end of 2015, Soundflower's original author Matt Ingalls picked up the baton. The project can now be found via this GitHub link. If you're looking to use Soundflower, that's the link to visit.
If you've previously used Soundflower, or are simply looking for a reliable tool to route audio between applications on your Mac, you may be interested in Loopback.
Loopback
Loopback is a modern, fully-featured virtual audio device tool of our own. With a robust infrastructure and full support, it's the ideal tool to route audio between applications and more.
Learn more on the Loopback page.
Symptoms: Some clients are unable to connect to the internet. Some clients report a different IP address, subnet mask and default gateway, compared to others.
Caveats: Without a managed switch fabric, this is considerably more difficult.
Diagnosis:
1. Allow a device to get an IP address from the rogue server. You might need to disable the main DHCP server to allow this to happen, as DHCP is a broadcast protocol, so it's really a case of the early bird getting the worm.
1b: Kyle Gordon pointed out that this initially assumes that the DHCP server is the same as the default gateway. He suggests: Usually /var/lib/dhcpcd/*.info or /var/lib/NetworkManager/* will contain the dhcp-server-identifier info on Linux, and something in the Windows Event Logs will show similar :-) Narcolepsy mac os.
2. Once you've got an IP from the rogue, look at the ethernet adaptor's status, and get the IP of the default gateway. For this example, we'll call it 10.1.1.1
3. Ping the default gateway for a few seconds. We need to do this to populate the ARP table.
4. In a Powershell/Cmd/Terminal window, run the command to view the ARP table. On windows, this is `arp -a`.
Swipey Rogue Mac Os Catalina
What you're looking for is the mapping between the IP address and the Physical (MAC) address.
5. Go to http://www.coffer.com/mac_find/ and paste the found Physical/MAC address of the rogue. This will tell you who made the device. Eternal dawn mac os.
This works because all MAC address prefixes are registered by IANA, so you can look up a MAC address and it'll tell you who made the thing (roughly).
6. From the client with the rogue-assigned IP address, set up a long-running ping to the default gateway. We'll need this to confirm that it's been killed when we start unplugging/disabling ports.
7. Next, you want to open the management pages of all of the switches on the fabric of your network. Every switch has a MAC Address Table where it keeps track of physical switchports, and the learned MAC addresses it's seen on those ports.
Swipey Rogue Mac Os Download
8. Looking at the list of address tables (I find it's helpful to copy/paste them into a text editor, then do a search on the MAC of the rogue.) see if you can track down a port that has *only* that MAC assigned to it. If there's a single port on a managed device, you can disable/shutdown the port.
9. Failing that, if you find that the MAC is in the table, but on a port with other devices too, say, port 1 has 5 other things, and the rogue is one of them, then that indicates that there's another distribution switch on port 1, and the rogue is connected to that.
Infinite (itch) (atlas) mac os. 10. Hopefully, you might have some clue as to what is on each port, distribution switch wise, especially if you have managed under-desk distribution switches, although this is generally unlikely.
11. Start hunting. You know that it's on the network, and can ping it (so you can tell when it's been disconnected). You know something about the device, the manufacturer.
12. As you unplug devices, check whether the ping stops.
13. When the ping stops, you've found the rogue.
14. Congratulate yourself by having a coffee, beer, or a non-stimulating beverage.
Swipey Rogue Mac Os Update
I actually worked through this process with one of my Astound Wireless customers, last night, over a VPN.
It's really relatively straight forward, but is made considerably easier with a managed switch fabric.
Swipey Rogue Mac Os X
In this case, the rogue turned out to be an Apple Airport Extreme, which do tend to cause havok if misconfigured, or misconnected, as their default is to broadcast DHCP on the 3 LAN ports, which aren't obvious that they're LAN ports, as they have the mysterious <-> symbol.
I suspect whomever plugged it into the network, should've connected the link to the building's switch fabric to the WAN port of the Airport Extreme, rather than the LAN. Or at the very least, disabled the DHCP server on the Airport.
An ideal solution for preventing this kind of mishap is DHCP snooping, but that *does* require a fully managed switch fabric, and a non-insignificant amount of management overhead.
